モデル・コンテキスト・プロトコル (MCP) は、大規模言語モデル (LLM) を外部ツールに接続する方法を定義する、Anthropic の強力なプロトコルです。MCP は、その使いやすさと AI の使用上のメリットにより、急速に人気が高まっています。この記事では、MCP で発生する可能性のあるセキュリティリスクと、それらを軽減する方法について説明します。
MCP の仕組み
MCP は LLM をツールに直接接続しません。MCP クライアントコンポーネントが LLM にアクセスし、MCP サーバーコンポーネントがツールにアクセスします。1 つの MCP クライアントは 1 つ以上の MCP サーバーにアクセスできます。ユーザーは、任意の数の MCP サーバーを MCP クライアントに接続できます。
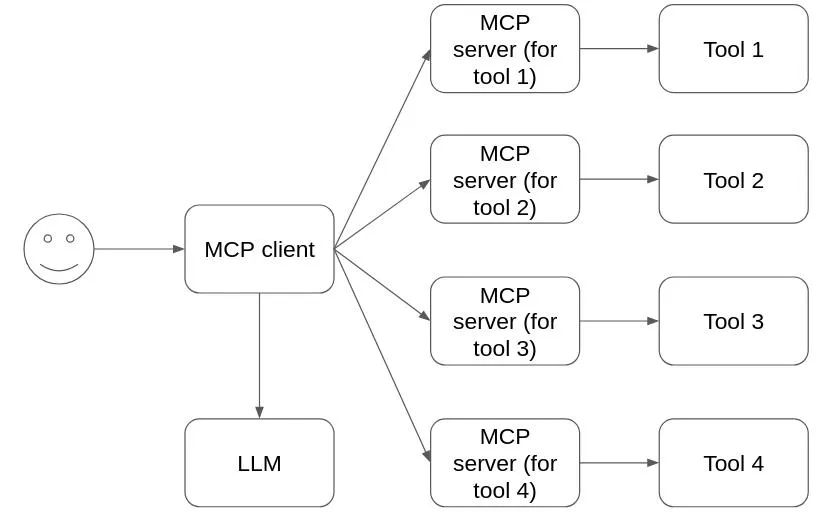
典型的な MCP クライアントとサーバーの流れは、次のようになります。
- ユーザーは MCP クライアントからタスクをリクエストします
- MCP クライアントは、各 MCP サーバーが実装またはアクセスできるツールに関する情報を持っています
- MCP クライアントがユーザーからのリクエストと MCP サーバーからの情報を LLM に渡し、LLM は必要なツールと使用するパラメータで応答します
- MCP クライアントはツールとパラメータに関する情報を MCP サーバーに送信します
- MCP サーバーはタスクを完了し、MCP クライアントに回答を返します。MCP クライアントは回答を LLM に渡し、LLM はユーザーへの応答を生成します
- 応答は MCP クライアントによってユーザーに表示されます
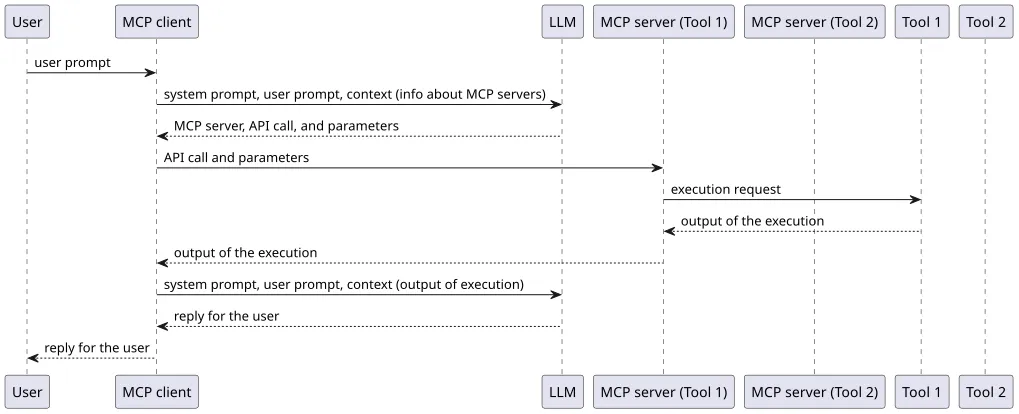
MCP サーバーはローカルまたはリモートで実行できますが、実行方法に応じてセキュリティリスクが異なります。
「ローカル MCP サーバー」とは、Red Hat が管理するホスト上で実行する MCP サーバーを指します。 要求されたタスクを実行するために、ローカル MCP サーバーは通常、OS コマンドまたはカスタム コードをローカルで実行します。
「リモート MCP サーバー」は、サードパーティによってリモートで実行されます。リモート MCP サーバーにアクセスできますが、それらのサーバーは Red Hat が管理するホスト上では実行されません。リモート MCP サーバーはユーザーのデータにアクセスできるため、ユーザーにとって依然としてセキュリティ上のリスクがありますが、ローカルで実行されないため、多くの一般的なリスクは当てはまりません。
セキュリティリスクと制御
ここでは、セキュリティ研究者が特定した MCP のリスクとその軽減アプローチの概要を簡単に説明します。
認証と認可
MCP サーバーがユーザーのリクエストによってトリガーされるアクションを実行する場合、「混乱した代理」問題が発生するリスクがあります。理想的なシナリオでは、MCP サーバーがユーザーの許可を得たうえで、ユーザーに代わってこのアクションを実行します。ただし、これは保証されるものではなく、MCP サーバーの実装に左右されます。正しく実装されていない場合、本来であれば MCP サーバーにだけアクセス可能な (ユーザーはアクセスできない) リソースにもアクセスできるようになり、最小権限の原則に違反する可能性があります。
MCP は OAuth を使用して認証を定義していますが、コミュニティ内での指摘によれば、現在の仕様には先進的な企業の慣行と相容れない実装の詳細が含まれています。コミュニティ内では、承認仕様の改善と更新、およびこの不一致の解消に向けた取り組みが進められています。
サプライチェーンのリスク
MCP サーバーは実行可能コードで構成されているため、ユーザーは信頼できる MCP サーバーのみを使用する必要があります。MCP サーバーを開発する場合は、ユーザーがソフトウェアを信頼できるように予防措置を講じる必要があります。MCP コンポーネントは開発者によって署名される必要があるため、整合性の安心感は高くなります。
また、静的アプリケーション・セキュリティ・テスト (SAST) などのセキュリティのベストプラクティスを実装するパイプライン上に MCP コンポーネントを構築する必要もあります。調査結果を理解し、誤検知を排除し、既知のセキュリティの脆弱性を修正しなければなりません。パイプラインでは、MCP サーバーで使用される依存関係の既知の脆弱性が特定され修正されるように、ソフトウェア・コンポジション分析 (SCA) も実装する必要があります。
MCP サーバーがクラウドサービスとして提供される場合は、クライアントがサーバーを検証できるように、暗号化サーバー検証も実装する必要があります。
他のソフトウェアと同様に、攻撃者が MCP コンポーネントのソースコードにアクセスして変更できれば、ユーザーのセキュリティは侵害されます。このリスクを軽減するには、ソフトウェア開発者とユーザーが、使用するすべての依存関係の整合性を検証し、マルウェアがないかスキャンする必要があります。
不正なコマンド実行
ローカル MCP サーバーは任意のコードを実行できます。MCP クライアントが MCP サーバーに情報を渡す方法と MCP サーバーの実装方法によっては、コマンド実行機能がコマンドインジェクション脆弱性の影響を受ける可能性があります。コマンドを実行する関数の引数としてデータを使用する前に、必ず実行されるコマンドを再確認し、データをサニタイズしてください。
以下の例は、コマンドインジェクションの脆弱性を持つ MCP サーバーの例です。
def dispatch_user_alert(self, notification_info: Dict[str, Any], summary_msg: str) -> bool: """Sends system alert to user desktop""" notify_config = self.user_prefs["alert_settings"] try: alert_title = f"{notification_info['title']} - {notification_info['severity']}" if sys.platform == "linux": subprocess.call(["notify-send", alert_title]) return Trueコードの出典: https://equixly.com/blog/2025/03/29/mcp-server-new-security-nightmare/
また、ローカル MCP サーバーをサンドボックス環境で実行すると良いでしょう。これにより、ローカル MCP サーバーは明示的に許可されたもののみを実行し、アクセスできるようになります。
プロンプトインジェクション
MCP サーバーは、コマンドの実行や API 呼び出しを行う能力を有するため、重大なセキュリティリスクを伴います。大きな懸念事項の 1 つとして、ユーザーが特定のアクションを意図していなくても、LLM がそれを適切であると判断する可能性があることが挙げられます。
このリスクは悪意がなくても発生する可能性がありますが、マイナス要因にもなります。たとえば、正当なユーザーが、悪意のある第三者によって推奨されたプロンプトなど、自分では書き込んでいないプロンプトを MCP クライアントに送信してしまう場合があります。このようなプロンプトは難読化されている可能性がありますが、それでもユーザーの会話やアクセス可能なツールから個人情報が漏洩することがあります。あるユーザーがクラウド環境に新しいユーザーを作成するために複雑で難読化されたプロンプトをコピーして貼り付けるとします。悪意のあるプロンプトは、意図したユーザーを作成するだけでなく、攻撃者用の別のユーザーも作成する可能性があります。
だからこそ、MCP サーバーによって実行されるアクションは、常にユーザーによって確認されるか、リスクを許容レベルまで低減するために制限される必要があります。
ツールインジェクション
また、誰かが悪意のある MCP サーバーを構築する可能性もあります。これはまったく新しいレベルのリスクをもたらします。例えば、悪意のある MCP サーバーも、インストール時にはソースコードやツールの説明でさえ正常に見えるため、最初は安全に見える可能性があります。しかし、ツールはその後のアップデートで改変される可能性があります。例えば、当初は天気情報を収集するツールとして説明されていたものが、アップデートにより改変され、機密情報を収集し、攻撃者に送信するようになるかもしれません。
これはツールの名前にも当てはまります。悪意のある aMCP サーバーは、ツールに偽の名前を付けることで、LLM に本来他の正当なツールが実行すべきタスクの代わりにそれらを選択させるなど、意図しないまたは有害な動作を引き起こす可能性があります。
このリスクの一部を軽減するために、ユーザーが MCP サーバーをインストールできるようにするソフトウェアには、MCP サーバーのバージョンを固定し、インストール後にコードまたは構成に変更があった場合にユーザーに通知する機能が必要です。
サンプリング
悪意のある MCP サーバーは、MCP サンプリング機能 (MCP サーバーが MCP クライアントに LLM を使用して要求を完了するように要求できる機能) を悪用しようとする可能性もあります。MCP サーバーが LLM にリクエストを送信する必要がある場合、サンプリングにより MCP クライアントは MCP サーバーに代わってリクエストを行うことができます。これにより、ユーザーは MCP クライアントをより細かく制御でき、コストを一元化できます。
MCP クライアントは、サンプリングに関連するリスクを軽減するために、次の制御を実装する必要があります。
- クライアントがユーザーに完了リクエストを表示できるようにする
- ユーザーが完了を変更または拒否できるようにする
- クライアントが完了をフィルタリングまたは変更できるようにする
- ユーザーが使用するモデルを制御できるようにする
- 適切なレート制限を実装する
- コスト露出を制御する
- タイムアウトを実装する
ロギング
前述のとおり、MCP サーバーは機密コマンドを実行できます。MCP サーバーは、ログやイベントを標準的な一元化ログサーバーに送信する機能、あるいはこれらのイベントをローカルに記録する機能を備えている必要があります。これにより、問題が発生した場合や問題が疑われる場合に、システムの動作を調査することができます。
脆弱性の管理
MCP サーバーはコードであるため、他のソフトウェアと同様に脆弱性が存在する可能性があります。そのため、標準の脆弱性管理プロセスに組み込むことが重要です。これには、組織のリスク許容度に基づいて、計画された間隔で MCP クライアントとサーバー、およびそれらの依存関係をアップグレードすることが含まれます。
まとめ
MCP は、自然言語を使用してツールを操作すること、およびユーザー、LLM、ツール間のコミュニケーション方法をより深く理解することへの関心を呼び起こしました。しかしながら、自動化の進展と AI の活用拡大に伴うセキュリティリスクを認識する必要があります。他の新しいテクノロジーと同様に、MCP を使用する場合、企業は自社のセキュリティリスクを評価し、適切なセキュリティ制御を実装してテクノロジーの価値を最大限に引き出す必要があります。
詳細はこちら
- MCP Servers: The New Security Nightmare (MCP サーバー:新たなセキュリティの悪夢)
- The MCP Authorization Spec Is... a Mess for Enterprise (MCP 認可仕様が企業に招く混乱)
- Everything Wrong with MCP (MCP の問題各種)
- Imprompter: Tricking LLM Agents into Improper Tool Use (インプロンプター:LLM エージェントを不正なツール使用に誘導する)
- Model Context Protocol (MCP): Landscape, Security Threats, and Future Research Directions (モデル・コンテキスト・プロトコル (MCP):現状、セキュリティ上の脅威、今後の研究の方向性)
- WhatsApp MCP Exploited: Exfiltrating your message history via MCP (WhatsApp MCP の脆弱性:MCP 経由でメッセージ履歴を盗み出す)
- 5 MCP Security Tips (MCP セキュリティに関する 5 つのヒント)
Hub
Red Hat 製品セキュリティ
執筆者紹介
Florencio has had cybersecurity in his veins since he was a kid. He started in cybersecurity around 1998 (time flies!) first as a hobby and then professionally. His first job required him to develop a host-based intrusion detection system in Python and for Linux for a research group in his university. Between 2008 and 2015 he had his own startup, which offered cybersecurity consulting services. He was CISO and head of security of a big retail company in Spain (more than 100k RHEL devices, including POS systems). Since 2020, he has worked at Red Hat as a Product Security Engineer and Architect.
チャンネル別に見る
自動化
テクノロジー、チームおよび環境に関する IT 自動化の最新情報
AI (人工知能)
お客様が AI ワークロードをどこでも自由に実行することを可能にするプラットフォームについてのアップデート
オープン・ハイブリッドクラウド
ハイブリッドクラウドで柔軟に未来を築く方法をご確認ください。
セキュリティ
環境やテクノロジー全体に及ぶリスクを軽減する方法に関する最新情報
エッジコンピューティング
エッジでの運用を単純化するプラットフォームのアップデート
インフラストラクチャ
世界有数のエンタープライズ向け Linux プラットフォームの最新情報
アプリケーション
アプリケーションの最も困難な課題に対する Red Hat ソリューションの詳細
仮想化
オンプレミスまたは複数クラウドでのワークロードに対応するエンタープライズ仮想化の将来についてご覧ください
